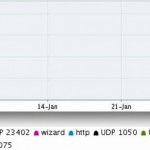
 69 percent of all DDoS attack traffic by bit volume in the first week of January was the result of NTP reflection. Black Lotus Miscreants who earlier this week took down servers for League of Legends, EA.com, and other online game services used a never-before-seen technique that vastly amplified the amount of junk traffic directed at denial-of-service targets. Rather than directly flooding the targeted services with torrents of data, an attack group calling itself DERP Trolling sent much smaller-sized data requests to time-synchronization servers running the Network Time Protocol (NTP). By manipulating the requests to make them appear as if they originated from one of the gaming sites, the attackers were able to vastly amplify the firepower at their disposal. A spoofed request containing eight bytes will typically result in a 468-byte response to victim, an increase of more than 58 fold. “Prior to December, an NTP attack was almost unheard of because if there was one it wasn’t worth talking about,” Shawn Marck, CEO of DoS-mitigation service Black Lotus , told Ars. “It was so tiny it never showed up in the major reports. What we’re witnessing is a shift in methodology.” Read 4 remaining paragraphs | Comments
69 percent of all DDoS attack traffic by bit volume in the first week of January was the result of NTP reflection. Black Lotus Miscreants who earlier this week took down servers for League of Legends, EA.com, and other online game services used a never-before-seen technique that vastly amplified the amount of junk traffic directed at denial-of-service targets. Rather than directly flooding the targeted services with torrents of data, an attack group calling itself DERP Trolling sent much smaller-sized data requests to time-synchronization servers running the Network Time Protocol (NTP). By manipulating the requests to make them appear as if they originated from one of the gaming sites, the attackers were able to vastly amplify the firepower at their disposal. A spoofed request containing eight bytes will typically result in a 468-byte response to victim, an increase of more than 58 fold. “Prior to December, an NTP attack was almost unheard of because if there was one it wasn’t worth talking about,” Shawn Marck, CEO of DoS-mitigation service Black Lotus , told Ars. “It was so tiny it never showed up in the major reports. What we’re witnessing is a shift in methodology.” Read 4 remaining paragraphs | Comments
More:
DoS attacks that took down big game sites abused Web’s time-sync protocol







Thanks for the post. The amount of DDoS attacks has increased dramatically over the last 10 years. Not everyone is going to agree with what everyone else is doing or has to say, but there are ways to protect your organisation from attack. A change in methodology is a curious thought but one that needs to be recognised and dealt with.