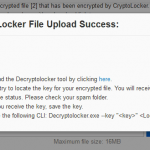
 Since file-encryption ransomware Crilock (also called CryptoLocker) has reared its head, the security industry has been hard at work finding ways to mitigate and neutralize these threats. We’ve also been hard at work finding ways to recover from the encryption and restore affected files – such as our recommendations on using version control and recovery options in SkyDrive and Windows . This week, researchers from FireEye and Fox-IT have released a tool that may be able to recover files encrypted by Crilock – without having to pay the malware authors. It’s important to note that the tool comes on the heels of a takedown of a Zeus/Gameover CnC server that was previously being used to authenticate and generate the encryption keys. This means the tool can only provide decryption keys for files that were encrypted by keys generated by that server. In other words, the tool comes with a caveat: it may not work in all instances. Ultimately, however, it’s still worth a try when you’ve tried everything else, and we want to share as many options and techniques to recover and protect your systems as possible The tool, created as a collaboration between FireEye and Fox-IT , is hosted at www.decryptcryptolocker.com (note that you’ll need to consent to their Terms of Use and Privacy Policy; Microsoft doesn’t own or operate the tool and we won’t be able to help you if it doesn’t work). The user uploads an encrypted file (it probably makes sense to use something without sensitive information or data) to the recovery portal, which searches for a matching private key from the database. If there is a match, the user receives an email with the actual private key which they can use to in a stand-alone command-line tool to decrypt each encrypted file on their own. Figure 1: Uploading a file to their online service We tested it out with files that were encrypted in November 2013 and received positive results (via email) for each file that was encrypted: Figure 2: Instructions from the DecryptCryptoLocker team Once downloaded, the tool can be launched with a command prompt: Decryptolocker.exe –key ” ” The command line operation would look like this (you just need to copy and paste the key from the email and specify the file): Figure 3: Decryption per file After applying the decryption key, you’ll receive an acknowledgement and consent request, and the file will be decrypted. Figure 4: File successfully decrypted It’s important to note that this tool will not work in every case – it depends on when the file was encrypted (and, therefore, if the CnC server that Crilock used was part of the takedown). You can read more about the tool at the FireEye blog Your locker of information for CryptoLocker decryption . Acknowledgements We would like to extend our thanks to colleagues at FireEye and Fox-IT for providing this kind of support for users whose files have been compromised by Crilock (CryptoLocker). Marianne Mallen MMPC Disclaimer The tool described in this blog is used at your risk. Read the instructions carefully on the tool’s website at https://www.decryptcryptolocker.com . In particular, note that you will be asked to consent to the site’s Terms of Use and the Privacy Policy. The site is not owned or operated by or affiliated with Microsoft. Follow us on Twitter ( @MSFTMMPC ) and like us on Facebook to get notifications of our blog posts and industry news.
Since file-encryption ransomware Crilock (also called CryptoLocker) has reared its head, the security industry has been hard at work finding ways to mitigate and neutralize these threats. We’ve also been hard at work finding ways to recover from the encryption and restore affected files – such as our recommendations on using version control and recovery options in SkyDrive and Windows . This week, researchers from FireEye and Fox-IT have released a tool that may be able to recover files encrypted by Crilock – without having to pay the malware authors. It’s important to note that the tool comes on the heels of a takedown of a Zeus/Gameover CnC server that was previously being used to authenticate and generate the encryption keys. This means the tool can only provide decryption keys for files that were encrypted by keys generated by that server. In other words, the tool comes with a caveat: it may not work in all instances. Ultimately, however, it’s still worth a try when you’ve tried everything else, and we want to share as many options and techniques to recover and protect your systems as possible The tool, created as a collaboration between FireEye and Fox-IT , is hosted at www.decryptcryptolocker.com (note that you’ll need to consent to their Terms of Use and Privacy Policy; Microsoft doesn’t own or operate the tool and we won’t be able to help you if it doesn’t work). The user uploads an encrypted file (it probably makes sense to use something without sensitive information or data) to the recovery portal, which searches for a matching private key from the database. If there is a match, the user receives an email with the actual private key which they can use to in a stand-alone command-line tool to decrypt each encrypted file on their own. Figure 1: Uploading a file to their online service We tested it out with files that were encrypted in November 2013 and received positive results (via email) for each file that was encrypted: Figure 2: Instructions from the DecryptCryptoLocker team Once downloaded, the tool can be launched with a command prompt: Decryptolocker.exe –key ” ” The command line operation would look like this (you just need to copy and paste the key from the email and specify the file): Figure 3: Decryption per file After applying the decryption key, you’ll receive an acknowledgement and consent request, and the file will be decrypted. Figure 4: File successfully decrypted It’s important to note that this tool will not work in every case – it depends on when the file was encrypted (and, therefore, if the CnC server that Crilock used was part of the takedown). You can read more about the tool at the FireEye blog Your locker of information for CryptoLocker decryption . Acknowledgements We would like to extend our thanks to colleagues at FireEye and Fox-IT for providing this kind of support for users whose files have been compromised by Crilock (CryptoLocker). Marianne Mallen MMPC Disclaimer The tool described in this blog is used at your risk. Read the instructions carefully on the tool’s website at https://www.decryptcryptolocker.com . In particular, note that you will be asked to consent to the site’s Terms of Use and the Privacy Policy. The site is not owned or operated by or affiliated with Microsoft. Follow us on Twitter ( @MSFTMMPC ) and like us on Facebook to get notifications of our blog posts and industry news.
Read More:
FireEye and Fox-IT tool can help recover Crilock-encrypted files