 Since the demise of DreamScene with Windows Vista, users have been denied the option of having moving pictures as their desktop backdrop, but the hugely useful VLC Media Player provides something of a workaround. Open up a movie then choose Video and Set as Wallpaper to place it behind your program windows, audio and all. Read more…
Since the demise of DreamScene with Windows Vista, users have been denied the option of having moving pictures as their desktop backdrop, but the hugely useful VLC Media Player provides something of a workaround. Open up a movie then choose Video and Set as Wallpaper to place it behind your program windows, audio and all. Read more…
Tag: microsoft
Tesla Model S Software Update Brings iPhone Unlocking And Ignition Start

 Tesla owners have been looking forward to OS 6.0, a software update for their vehicles, for a while now, but it’s finally rolling out to vehicle owners, reports Electrek. The system adds a bunch of new features for Model S vehicles, including a new Calendar app for in-car use, and big improvements to the Maps/Navigation software. What’s amazing (and surprising) for iPhone users is… Read More
Tesla owners have been looking forward to OS 6.0, a software update for their vehicles, for a while now, but it’s finally rolling out to vehicle owners, reports Electrek. The system adds a bunch of new features for Model S vehicles, including a new Calendar app for in-car use, and big improvements to the Maps/Navigation software. What’s amazing (and surprising) for iPhone users is… Read More
See original article:
Tesla Model S Software Update Brings iPhone Unlocking And Ignition Start
Watch a Cat Video, Get Hacked: the Death of Clear-Text

![]() New submitter onproton writes: Citizen Lab released new research today on a targeted exploitation technique used by state actors involving “network injection appliances” installed at ISPs. These devices can target and intercept unencrypted YouTube traffic and replace it with malicious code that gives the operator control over the system or installs a surveillance backdoor. One of the researchers writes, “many otherwise well-informed people think they have to do something wrong, or stupid, or insecure to get hacked—like clicking on the wrong attachments, or browsing malicious websites…many of these commonly held beliefs are not necessarily true.” This technique is largely designed for targeted attacks, so it’s likely most of us will be safe for now — but just one more reminder to use https. Read more of this story at Slashdot.
New submitter onproton writes: Citizen Lab released new research today on a targeted exploitation technique used by state actors involving “network injection appliances” installed at ISPs. These devices can target and intercept unencrypted YouTube traffic and replace it with malicious code that gives the operator control over the system or installs a surveillance backdoor. One of the researchers writes, “many otherwise well-informed people think they have to do something wrong, or stupid, or insecure to get hacked—like clicking on the wrong attachments, or browsing malicious websites…many of these commonly held beliefs are not necessarily true.” This technique is largely designed for targeted attacks, so it’s likely most of us will be safe for now — but just one more reminder to use https. Read more of this story at Slashdot.
Originally posted here:
Watch a Cat Video, Get Hacked: the Death of Clear-Text
AirEnergy Is An Upgradable Wind Turbine You Can Keep In A Backpack

 Have you ever wanted to become a self-sufficient hermit, living off the grid and generating all your own energy? Well you can stop drying out and burning your number-twos because here comes AirEnergy 3D. This Polish crowdfunding project is a compact, portable, and upgradable wind turbine that consists of blades and a base station. Created by the folks at Omni3D, a 3D printer manufacturer… Read More
Have you ever wanted to become a self-sufficient hermit, living off the grid and generating all your own energy? Well you can stop drying out and burning your number-twos because here comes AirEnergy 3D. This Polish crowdfunding project is a compact, portable, and upgradable wind turbine that consists of blades and a base station. Created by the folks at Omni3D, a 3D printer manufacturer… Read More
Continue reading here:
AirEnergy Is An Upgradable Wind Turbine You Can Keep In A Backpack
FireEye and Fox-IT tool can help recover Crilock-encrypted files
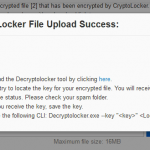
 Since file-encryption ransomware Crilock (also called CryptoLocker) has reared its head, the security industry has been hard at work finding ways to mitigate and neutralize these threats. We’ve also been hard at work finding ways to recover from the encryption and restore affected files – such as our recommendations on using version control and recovery options in SkyDrive and Windows . This week, researchers from FireEye and Fox-IT have released a tool that may be able to recover files encrypted by Crilock – without having to pay the malware authors. It’s important to note that the tool comes on the heels of a takedown of a Zeus/Gameover CnC server that was previously being used to authenticate and generate the encryption keys. This means the tool can only provide decryption keys for files that were encrypted by keys generated by that server. In other words, the tool comes with a caveat: it may not work in all instances. Ultimately, however, it’s still worth a try when you’ve tried everything else, and we want to share as many options and techniques to recover and protect your systems as possible The tool, created as a collaboration between FireEye and Fox-IT , is hosted at www.decryptcryptolocker.com (note that you’ll need to consent to their Terms of Use and Privacy Policy; Microsoft doesn’t own or operate the tool and we won’t be able to help you if it doesn’t work). The user uploads an encrypted file (it probably makes sense to use something without sensitive information or data) to the recovery portal, which searches for a matching private key from the database. If there is a match, the user receives an email with the actual private key which they can use to in a stand-alone command-line tool to decrypt each encrypted file on their own. Figure 1: Uploading a file to their online service We tested it out with files that were encrypted in November 2013 and received positive results (via email) for each file that was encrypted: Figure 2: Instructions from the DecryptCryptoLocker team Once downloaded, the tool can be launched with a command prompt: Decryptolocker.exe –key ” ” The command line operation would look like this (you just need to copy and paste the key from the email and specify the file): Figure 3: Decryption per file After applying the decryption key, you’ll receive an acknowledgement and consent request, and the file will be decrypted. Figure 4: File successfully decrypted It’s important to note that this tool will not work in every case – it depends on when the file was encrypted (and, therefore, if the CnC server that Crilock used was part of the takedown). You can read more about the tool at the FireEye blog Your locker of information for CryptoLocker decryption . Acknowledgements We would like to extend our thanks to colleagues at FireEye and Fox-IT for providing this kind of support for users whose files have been compromised by Crilock (CryptoLocker). Marianne Mallen MMPC Disclaimer The tool described in this blog is used at your risk. Read the instructions carefully on the tool’s website at https://www.decryptcryptolocker.com . In particular, note that you will be asked to consent to the site’s Terms of Use and the Privacy Policy. The site is not owned or operated by or affiliated with Microsoft. Follow us on Twitter ( @MSFTMMPC ) and like us on Facebook to get notifications of our blog posts and industry news.
Since file-encryption ransomware Crilock (also called CryptoLocker) has reared its head, the security industry has been hard at work finding ways to mitigate and neutralize these threats. We’ve also been hard at work finding ways to recover from the encryption and restore affected files – such as our recommendations on using version control and recovery options in SkyDrive and Windows . This week, researchers from FireEye and Fox-IT have released a tool that may be able to recover files encrypted by Crilock – without having to pay the malware authors. It’s important to note that the tool comes on the heels of a takedown of a Zeus/Gameover CnC server that was previously being used to authenticate and generate the encryption keys. This means the tool can only provide decryption keys for files that were encrypted by keys generated by that server. In other words, the tool comes with a caveat: it may not work in all instances. Ultimately, however, it’s still worth a try when you’ve tried everything else, and we want to share as many options and techniques to recover and protect your systems as possible The tool, created as a collaboration between FireEye and Fox-IT , is hosted at www.decryptcryptolocker.com (note that you’ll need to consent to their Terms of Use and Privacy Policy; Microsoft doesn’t own or operate the tool and we won’t be able to help you if it doesn’t work). The user uploads an encrypted file (it probably makes sense to use something without sensitive information or data) to the recovery portal, which searches for a matching private key from the database. If there is a match, the user receives an email with the actual private key which they can use to in a stand-alone command-line tool to decrypt each encrypted file on their own. Figure 1: Uploading a file to their online service We tested it out with files that were encrypted in November 2013 and received positive results (via email) for each file that was encrypted: Figure 2: Instructions from the DecryptCryptoLocker team Once downloaded, the tool can be launched with a command prompt: Decryptolocker.exe –key ” ” The command line operation would look like this (you just need to copy and paste the key from the email and specify the file): Figure 3: Decryption per file After applying the decryption key, you’ll receive an acknowledgement and consent request, and the file will be decrypted. Figure 4: File successfully decrypted It’s important to note that this tool will not work in every case – it depends on when the file was encrypted (and, therefore, if the CnC server that Crilock used was part of the takedown). You can read more about the tool at the FireEye blog Your locker of information for CryptoLocker decryption . Acknowledgements We would like to extend our thanks to colleagues at FireEye and Fox-IT for providing this kind of support for users whose files have been compromised by Crilock (CryptoLocker). Marianne Mallen MMPC Disclaimer The tool described in this blog is used at your risk. Read the instructions carefully on the tool’s website at https://www.decryptcryptolocker.com . In particular, note that you will be asked to consent to the site’s Terms of Use and the Privacy Policy. The site is not owned or operated by or affiliated with Microsoft. Follow us on Twitter ( @MSFTMMPC ) and like us on Facebook to get notifications of our blog posts and industry news.
Read More:
FireEye and Fox-IT tool can help recover Crilock-encrypted files
Chicago Mayor Praises Google For Buying Kids Microsoft Surfaces

![]() theodp (442580) writes “Google earned kudos from Chicago Mayor Rahm Emanuel this week for teaming up with Staples to fund the projects of 367 of the city’s 22, 519 public school teachers on “begfunding” site DonorsChoose.org. “Everything that you asked for…every project that the teachers put on to help their students learn, exceed and excel here in the city of Chicago, you now have fully funded, ” Mayor Emanuel said. “Chicago’s hardworking public school teachers are doing all that they can-and more-to support their students, but they need more help, ” said Rob Biederman, head of Chicago Public Affairs at Google. “We jumped at the chance to join with DonorsChoose.org and Staples to make Chicago’s local classroom wishes come true.” So what kind of dreams did Google make possible? Ironically, a look at Google Chicago’s Giving Page shows that the biggest project funded by Google was to outfit a classroom with 32 Microsoft Surface RT tablets for $12, 531, or about 6.5% of the $190, 091 Google award. Other big ticket projects funded by Google included $5, 931 for a personal home biodiesel kit and $5, 552 for a marimba (in the middle of the spectrum was $748 for “Mindfulness Education”). In addition to similar “flash-funding” projects in Atlanta (paper towels!) and the Bay Area, Google and DonorsChoose have also teamed up this year to reward teachers with $400, 000 for recruiting girls to learn to code (part of Google’s $50 million Made With Code initiative) and an unknown amount for AP STEM teachers who passed Google muster (part of Google’s $5 million AP STEM Access grant).” Read more of this story at Slashdot.
theodp (442580) writes “Google earned kudos from Chicago Mayor Rahm Emanuel this week for teaming up with Staples to fund the projects of 367 of the city’s 22, 519 public school teachers on “begfunding” site DonorsChoose.org. “Everything that you asked for…every project that the teachers put on to help their students learn, exceed and excel here in the city of Chicago, you now have fully funded, ” Mayor Emanuel said. “Chicago’s hardworking public school teachers are doing all that they can-and more-to support their students, but they need more help, ” said Rob Biederman, head of Chicago Public Affairs at Google. “We jumped at the chance to join with DonorsChoose.org and Staples to make Chicago’s local classroom wishes come true.” So what kind of dreams did Google make possible? Ironically, a look at Google Chicago’s Giving Page shows that the biggest project funded by Google was to outfit a classroom with 32 Microsoft Surface RT tablets for $12, 531, or about 6.5% of the $190, 091 Google award. Other big ticket projects funded by Google included $5, 931 for a personal home biodiesel kit and $5, 552 for a marimba (in the middle of the spectrum was $748 for “Mindfulness Education”). In addition to similar “flash-funding” projects in Atlanta (paper towels!) and the Bay Area, Google and DonorsChoose have also teamed up this year to reward teachers with $400, 000 for recruiting girls to learn to code (part of Google’s $50 million Made With Code initiative) and an unknown amount for AP STEM teachers who passed Google muster (part of Google’s $5 million AP STEM Access grant).” Read more of this story at Slashdot.
Read the original:
Chicago Mayor Praises Google For Buying Kids Microsoft Surfaces
F-Secure: Xiaomi Smartphones Do Secretly Steal Your Data

![]() They may be well reviewed and China’s new top selling phone, but reader DavidGilbert99 writes with reason to be cautious about Xiaomi’s phones: Finnish security firm F-Secure has seemingly proven that Xiaomi smartphones do in fact upload user data without their permission/knowledge despite the company strongly denying these allegations as late as 30 July. Between commercial malware and government agencies, how do you keep your phone’s data relatively private? Read more of this story at Slashdot.
They may be well reviewed and China’s new top selling phone, but reader DavidGilbert99 writes with reason to be cautious about Xiaomi’s phones: Finnish security firm F-Secure has seemingly proven that Xiaomi smartphones do in fact upload user data without their permission/knowledge despite the company strongly denying these allegations as late as 30 July. Between commercial malware and government agencies, how do you keep your phone’s data relatively private? Read more of this story at Slashdot.
Originally posted here:
F-Secure: Xiaomi Smartphones Do Secretly Steal Your Data
Cornering the Market On Zero-Day Exploits

![]() Nicola Hahn (1482985) writes Kim Zetter of Wired Magazine has recently covered Dan Greer’s keynote speech at Black Hat USA. In his lengthy address Greer, representing the CIA’s venture funding arm, suggested that one way that the United States government could improve cyber security would be to use its unparalleled budget to buy up all the underground’s zero-day vulnerabilities. While this would no doubt make zero-day vendors like VUPEN and middlemen like the Grugq very wealthy, is this strategy really a good idea? Can the public really trust the NSA to do the right thing with all those zero-day exploits? Furthermore, recall the financial meltdown of 2008 where the public paid the bill for Wall Street’s greed. If the government pays for information on all these unpatched bugs would society simply be socializing the cost of hi-tech’s sloppy engineering? Whose interests does this “corner-the-market” approach actually serve? Read more of this story at Slashdot.
Nicola Hahn (1482985) writes Kim Zetter of Wired Magazine has recently covered Dan Greer’s keynote speech at Black Hat USA. In his lengthy address Greer, representing the CIA’s venture funding arm, suggested that one way that the United States government could improve cyber security would be to use its unparalleled budget to buy up all the underground’s zero-day vulnerabilities. While this would no doubt make zero-day vendors like VUPEN and middlemen like the Grugq very wealthy, is this strategy really a good idea? Can the public really trust the NSA to do the right thing with all those zero-day exploits? Furthermore, recall the financial meltdown of 2008 where the public paid the bill for Wall Street’s greed. If the government pays for information on all these unpatched bugs would society simply be socializing the cost of hi-tech’s sloppy engineering? Whose interests does this “corner-the-market” approach actually serve? Read more of this story at Slashdot.
Visit site:
Cornering the Market On Zero-Day Exploits
Microsoft’s First Website From 1994 Looks Delightfully Ancient Today
 In 1994, there were just a few thousand websites on the internet. HTML was still new, and the concept of web publishing was still embryonic. It was the year that Microsoft launched its own website—and today, to celebrate its 20th anniversary on the web, it dug it up and put it back online . Read more…
In 1994, there were just a few thousand websites on the internet. HTML was still new, and the concept of web publishing was still embryonic. It was the year that Microsoft launched its own website—and today, to celebrate its 20th anniversary on the web, it dug it up and put it back online . Read more…
View article:
Microsoft’s First Website From 1994 Looks Delightfully Ancient Today
Facebook Seeks Devs To Make Linux Network Stack As Good As FreeBSD’s

![]() An anonymous reader writes Facebook posted a career application which, in their own words is ‘seeking a Linux Kernel Software Engineer to join our Kernel team, with a primary focus on the networking subsystem. Our goal over the next few years is for the Linux kernel network stack to rival or exceed that of FreeBSD.’ Two interesting bullet points listing “responsibilities”: Improve IPv6 support in the kernel, and eliminate perf and stability issues. FB is one of the worlds largest IPv6 deployments; Investigate and participate in emerging protocols (MPTCP, QUIC, etc) discussions, implementation, experimentation, tooling, etc. Read more of this story at Slashdot.
An anonymous reader writes Facebook posted a career application which, in their own words is ‘seeking a Linux Kernel Software Engineer to join our Kernel team, with a primary focus on the networking subsystem. Our goal over the next few years is for the Linux kernel network stack to rival or exceed that of FreeBSD.’ Two interesting bullet points listing “responsibilities”: Improve IPv6 support in the kernel, and eliminate perf and stability issues. FB is one of the worlds largest IPv6 deployments; Investigate and participate in emerging protocols (MPTCP, QUIC, etc) discussions, implementation, experimentation, tooling, etc. Read more of this story at Slashdot.
Continue reading here:
Facebook Seeks Devs To Make Linux Network Stack As Good As FreeBSD’s