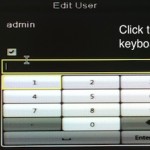
 The dialog that appears when users want to manually change the default password on their EPCOM Hikvision S04 DVR. Sans Institute It took just one day for a low-end, Internet-connected digital video recorder to become infected with malware that surreptitiously mined Bitcoins on behalf of the quick-moving attackers. The feat, documented in a blog post published Monday by researchers at the security-training outfit Sans Institute, was all the more impressive because the DVR contained no interface for downloading software from the Internet. The lack of a Wget , ftp, or kermit application posed little challenge for the attackers. To work around the limitation, the miscreants used a series of Unix commands that effectively uploaded and executed a Wget package and then used it to retrieve the Bitcoin miner from an Internet-connected server. Monday’s observations from Sans CTO Johannes Ullrich are part of an ongoing series showing the increasing vulnerability of Internet-connected appliances to malware attacks. In this case, he bought an EPCOM Hikvision S04 DVR off eBay, put it into what he believes was its factory new condition, and connected it to a laboratory “honeypot” where it was susceptible to online attackers. In the first day, it was probed by 13 different IP addresses, six of which were able to log into it using the default username and password combination of “root” and “12345.” Read 4 remaining paragraphs | Comments
The dialog that appears when users want to manually change the default password on their EPCOM Hikvision S04 DVR. Sans Institute It took just one day for a low-end, Internet-connected digital video recorder to become infected with malware that surreptitiously mined Bitcoins on behalf of the quick-moving attackers. The feat, documented in a blog post published Monday by researchers at the security-training outfit Sans Institute, was all the more impressive because the DVR contained no interface for downloading software from the Internet. The lack of a Wget , ftp, or kermit application posed little challenge for the attackers. To work around the limitation, the miscreants used a series of Unix commands that effectively uploaded and executed a Wget package and then used it to retrieve the Bitcoin miner from an Internet-connected server. Monday’s observations from Sans CTO Johannes Ullrich are part of an ongoing series showing the increasing vulnerability of Internet-connected appliances to malware attacks. In this case, he bought an EPCOM Hikvision S04 DVR off eBay, put it into what he believes was its factory new condition, and connected it to a laboratory “honeypot” where it was susceptible to online attackers. In the first day, it was probed by 13 different IP addresses, six of which were able to log into it using the default username and password combination of “root” and “12345.” Read 4 remaining paragraphs | Comments
View article:
Infecting DVRs with Bitcoin-mining malware even easier than you suspected





