 An anonymous reader quotes the Bay Area Newsgroup: Wells Fargo may have opened as many as 3.5 million bogus bank accounts without its customers’ permission, attorneys for customers suing the bank have alleged in a court filing, suggesting the bank may have created far more fake accounts than previously indicated. The plaintiffs’ new estimate of bogus bank accounts is about 1.4 million, or 67%, higher than the original estimate — disclosed last year as part of a settlement with regulators — that up to 2.1 million accounts were opened without customers’ permission… The attorneys covered a period from 2002 to 2017, rather than the previously scrutinized five-year stretch from 2011 to some time in 2016 in which the bank acknowledged setting up unauthorized accounts. Wells Fargo terminated 5, 300 employees for creating fake accounts, and their CEO now acknowledges that “we had an incentive program and a high-pressure sales culture within our community bank that drove behavior that many times was inappropriate and inconsistent with our values.” In a possibly-related story, Wells Fargo plans to shut 450 branches over the next two years. Read more of this story at Slashdot.
An anonymous reader quotes the Bay Area Newsgroup: Wells Fargo may have opened as many as 3.5 million bogus bank accounts without its customers’ permission, attorneys for customers suing the bank have alleged in a court filing, suggesting the bank may have created far more fake accounts than previously indicated. The plaintiffs’ new estimate of bogus bank accounts is about 1.4 million, or 67%, higher than the original estimate — disclosed last year as part of a settlement with regulators — that up to 2.1 million accounts were opened without customers’ permission… The attorneys covered a period from 2002 to 2017, rather than the previously scrutinized five-year stretch from 2011 to some time in 2016 in which the bank acknowledged setting up unauthorized accounts. Wells Fargo terminated 5, 300 employees for creating fake accounts, and their CEO now acknowledges that “we had an incentive program and a high-pressure sales culture within our community bank that drove behavior that many times was inappropriate and inconsistent with our values.” In a possibly-related story, Wells Fargo plans to shut 450 branches over the next two years. Read more of this story at Slashdot.
View article:
Up To 1.4M More Fake Wells Fargo Accounts Possible
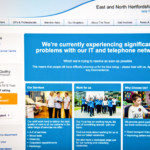 England’s healthcare system came under a withering cyberattack Friday morning, with ” at least 25 ” hospitals across the country falling prey to ransomware that locked doctors and employees out of critical systems and networks. The UK government now reports that this is not a (relatively) isolated attack but rather a single front in a massive regionwide digital assault. #nhscyberattack pic.twitter.com/SovgQejl3X — gigi.h (@fendifille) May 12, 2017 The attack has impacted hospitals and transportation infrastructure across Europe, Russia and Asia. Organizations in dozens of countries have all been hit with the same ransomware program, a variant of the WannaCry virus, spouting the same ransom note and demanding $300 for the encryption key, with the demand escalating as time passes. The virus’s infection vector appears to through a known vulnerability, originally exploited and developed by the National Security Agency. That information was subsequently leaked by the hacking group known as Shadow Broker which has been dumping its cache of purloined NSA hacking tools onto the internet since last year. The virus appears to have originally spread via email as compressed file attachment so, like last week’s Google Docs issue, make sure you confirm that you email’s attachments are legit before clicking on them. Also, make sure your computers are using software that’s still receiving security updates, and that you’ve installed the latest updates available. Microsoft released a fix for the exploit used as a part of its March “Patch Tuesday” release, but unpatched Windows systems remain vulnerable. Update : Reuters reports a statement from Microsoft indicating that engineers have added detection and protection against the “Ransom:Win32.WannaCrypt” malware, so make sure your Windows Defender or other antivirus is updated before logging on to any corporate networks that may be infected. In a statement, a FedEx representative confirmed its systems are being impacted, saying “Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware. We are implementing remediation steps as quickly as possible. We regret any inconvenience to our customers.” Source: New York Times
England’s healthcare system came under a withering cyberattack Friday morning, with ” at least 25 ” hospitals across the country falling prey to ransomware that locked doctors and employees out of critical systems and networks. The UK government now reports that this is not a (relatively) isolated attack but rather a single front in a massive regionwide digital assault. #nhscyberattack pic.twitter.com/SovgQejl3X — gigi.h (@fendifille) May 12, 2017 The attack has impacted hospitals and transportation infrastructure across Europe, Russia and Asia. Organizations in dozens of countries have all been hit with the same ransomware program, a variant of the WannaCry virus, spouting the same ransom note and demanding $300 for the encryption key, with the demand escalating as time passes. The virus’s infection vector appears to through a known vulnerability, originally exploited and developed by the National Security Agency. That information was subsequently leaked by the hacking group known as Shadow Broker which has been dumping its cache of purloined NSA hacking tools onto the internet since last year. The virus appears to have originally spread via email as compressed file attachment so, like last week’s Google Docs issue, make sure you confirm that you email’s attachments are legit before clicking on them. Also, make sure your computers are using software that’s still receiving security updates, and that you’ve installed the latest updates available. Microsoft released a fix for the exploit used as a part of its March “Patch Tuesday” release, but unpatched Windows systems remain vulnerable. Update : Reuters reports a statement from Microsoft indicating that engineers have added detection and protection against the “Ransom:Win32.WannaCrypt” malware, so make sure your Windows Defender or other antivirus is updated before logging on to any corporate networks that may be infected. In a statement, a FedEx representative confirmed its systems are being impacted, saying “Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware. We are implementing remediation steps as quickly as possible. We regret any inconvenience to our customers.” Source: New York Times