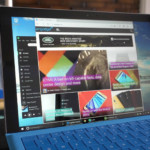
 If the idea of a more secure Windows browser appeals to you — and why wouldn’t it — then you might want to have a peek at the latest Windows 10 Insider Preview Build . That’s because it includes the Windows Defender Application Guard for Microsoft Edge, which was announced last September but is finally available for testing today. This Application Guard essentially encases your browser in a virtual machine, so that if your browser ever gets attacked by malware, it won’t affect the rest of your PC. To enable this, you need to use the “Turn Windows features on or off” dialog, and then mark the checkbox for “Windows Defender Application Guard.” Now when you open Microsoft Edge and click on the menu, you’ll see the option for a “New Application Guard window.” Click it, and a new special isolated browser window will appear. The whole thing is possible due to the Virtualization Based Security (VBS) made possible by Windows 10. The virtual PC created by Application Guard would keep the Edge browser separate from storage, other apps and the Windows 10 kernel. Other browsers offer “sandboxes” too, but Microsoft says that Application Guard is unique because there’s a hardware container that makes it impossible for malware and other exploits to seep through. There are a couple of caveats though. Running Edge in a virtual machine will likely slow it down, and since each browser’s session is siloed, all data and cookies are lost once you close it. It’s also only available for Enterprise users for now, presumably because their security needs are much higher than the average person. Still, perhaps it could be introduced as an optional feature later on for everyday users. Aside from Application Guard, the Windows 10 Insider Preview Build also includes an improved PDF Reader for Microsoft Edge and integrated Cortana settings.
If the idea of a more secure Windows browser appeals to you — and why wouldn’t it — then you might want to have a peek at the latest Windows 10 Insider Preview Build . That’s because it includes the Windows Defender Application Guard for Microsoft Edge, which was announced last September but is finally available for testing today. This Application Guard essentially encases your browser in a virtual machine, so that if your browser ever gets attacked by malware, it won’t affect the rest of your PC. To enable this, you need to use the “Turn Windows features on or off” dialog, and then mark the checkbox for “Windows Defender Application Guard.” Now when you open Microsoft Edge and click on the menu, you’ll see the option for a “New Application Guard window.” Click it, and a new special isolated browser window will appear. The whole thing is possible due to the Virtualization Based Security (VBS) made possible by Windows 10. The virtual PC created by Application Guard would keep the Edge browser separate from storage, other apps and the Windows 10 kernel. Other browsers offer “sandboxes” too, but Microsoft says that Application Guard is unique because there’s a hardware container that makes it impossible for malware and other exploits to seep through. There are a couple of caveats though. Running Edge in a virtual machine will likely slow it down, and since each browser’s session is siloed, all data and cookies are lost once you close it. It’s also only available for Enterprise users for now, presumably because their security needs are much higher than the average person. Still, perhaps it could be introduced as an optional feature later on for everyday users. Aside from Application Guard, the Windows 10 Insider Preview Build also includes an improved PDF Reader for Microsoft Edge and integrated Cortana settings.
Read More:
Microsoft tests a secured Edge browser for business


 An anonymous reader writes: A recently released draft of the National Institute of Standards and Technology’s digital identity guidelines has met with approval by vendors. The draft guidelines revise password security recommendations and altering many of the standards and best practices security professionals use when forming policies for their companies. The new framework recommends, among other things: “Remove periodic password change requirements.” There have been multiple studies that have shown requiring frequent password changes to actually be counterproductive to good password security, said Mike Wilson, founder of PasswordPing. NIST said this guideline was suggested because passwords should be changed when a user wants to change it or if there is indication of breach. Read more of this story at Slashdot.
An anonymous reader writes: A recently released draft of the National Institute of Standards and Technology’s digital identity guidelines has met with approval by vendors. The draft guidelines revise password security recommendations and altering many of the standards and best practices security professionals use when forming policies for their companies. The new framework recommends, among other things: “Remove periodic password change requirements.” There have been multiple studies that have shown requiring frequent password changes to actually be counterproductive to good password security, said Mike Wilson, founder of PasswordPing. NIST said this guideline was suggested because passwords should be changed when a user wants to change it or if there is indication of breach. Read more of this story at Slashdot.